It does work both ways, as the theory states that competent individuals were more humble and underestimated their skills.
bbbhltz
If I'm correct, that would mean that technically, I could authenticate to an SSH server without supplying my name if I use a private key?
Yes.
The public key contains a user name/email address string, I'm aware, is the same information also encoded into the private key as well? If yes, I don't see the need to hand that info to an SSH call. If no, how does the SSH server know which public key it's supposed to use to challenge my private key ownership?
Most of this can be found reading through different Git docs, whether from GitHub, GitLab, Codeberg, Gitea, etc. When using Git you can use different keys for different repos/forges and each has a defined pair, similar to accessing different SSH servers that require specific key pairs. I do understand your questions, but I lack the finesse to explain it since I really only use SSH and Git for my blog and not for anything too complicated.
There are some tips here that might help
https://github.com/dajeed/arch-linux-font-improvement-guide
Important to note that restarting or running sudo fc-cache -fv is key when doing things with fonts.
An old friend of mine that I've lost touch with is Chinese. They lived in Europe for a number of years. When they couldn't get a new job their visa ran out and the went back home.
No problem getting a job. They had a place to live. Things were good.
But... When they left Europe they basically told their roommate, a student who was about 10 years their younger, that they were leaving and that's it. They abandoned the apartment. This left not only rent up to the student, but also the €300 fee of changing the name on the rental contract.
If a police investigation is launched against someone in China, you can be damned sure they will turn up something. If this influencer ever saw a doobie they will find out, and if they never did drugs they will find an acquaintance who did.
I say this because one day when my friend left work there was a car waiting. It was the father of her roommate. Turns out he was a "special" police officer. He told them to get in and gave her a folder. The folder had photos of them, their friends, even me. There were notes on the friends, SMS and social media exchanges. This included references to drugs. He took them to a bank, told them to take out the equivalent of €900 (he had their bank statements already) or their family would hear about this...and then he left them there on the street.
There are solutions that work. Like you, I would enjoy a simple app that allows for subscriptions and playlists without tracking or using an account. I mostly use RSS feeds (newsboat) and watch the videos through mpv.
And yt-fzf is great too. It uses invidious instances instead of YouTube links.
I don't feel like my system is bloated.
It probably isn't bloated.
I guess it's subjective, but when do you consider a system to be bloated?
If someone is testing out several different DEs or WMs and installing meta-packages, then I suppose I might say that things are bloated because they could end up having multiple apps to control the same preferences along with different libraries, etc., and then when they decide to update it takes ages. That would be bloated for me. I have tried the minimal stuff before. Like you said, hundreds of packages, not thousands. But, I didn't install any manpages. So when I decided I wanted those manpages the number of packages ballooned. Nothing was really bloated, just a number on neofetch going up.
Content mills...
Just go to the source. The dev is sharing more info and videos. Sure, it is on LinkedIn which is rubbish but at least it isn't 9to5Linux
Strawberry Music Player has smart and dynamic playlist generators. I cannot say how well they work.
The package manager for Alpine is...so fast. The community (IRC/Gitlab) is responsive and helpful.
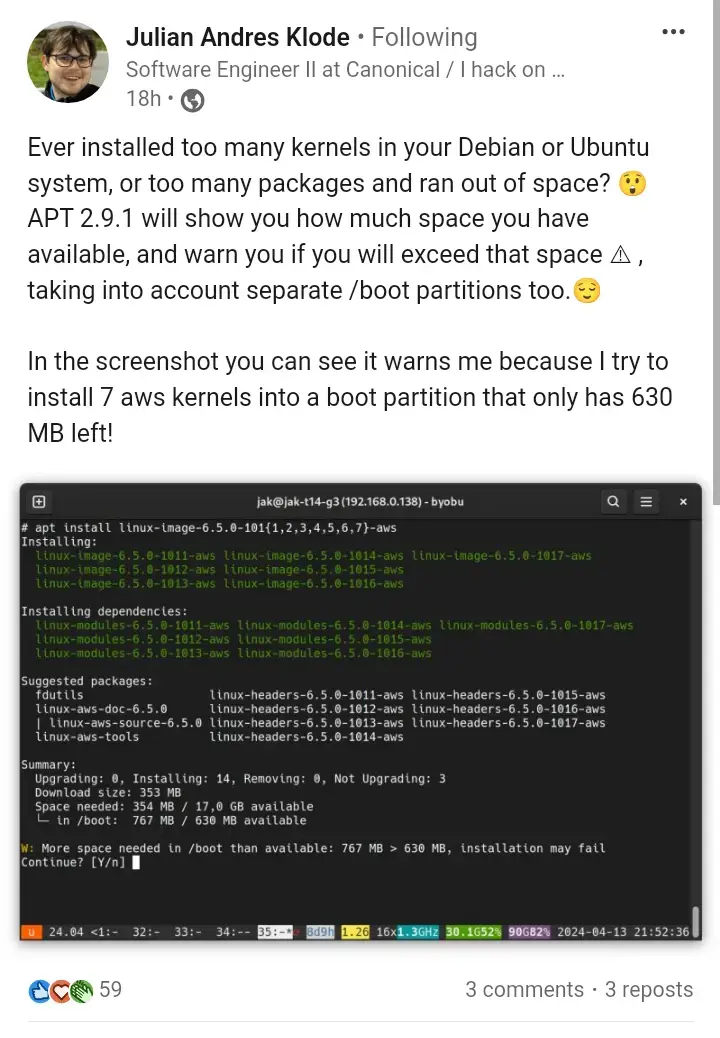
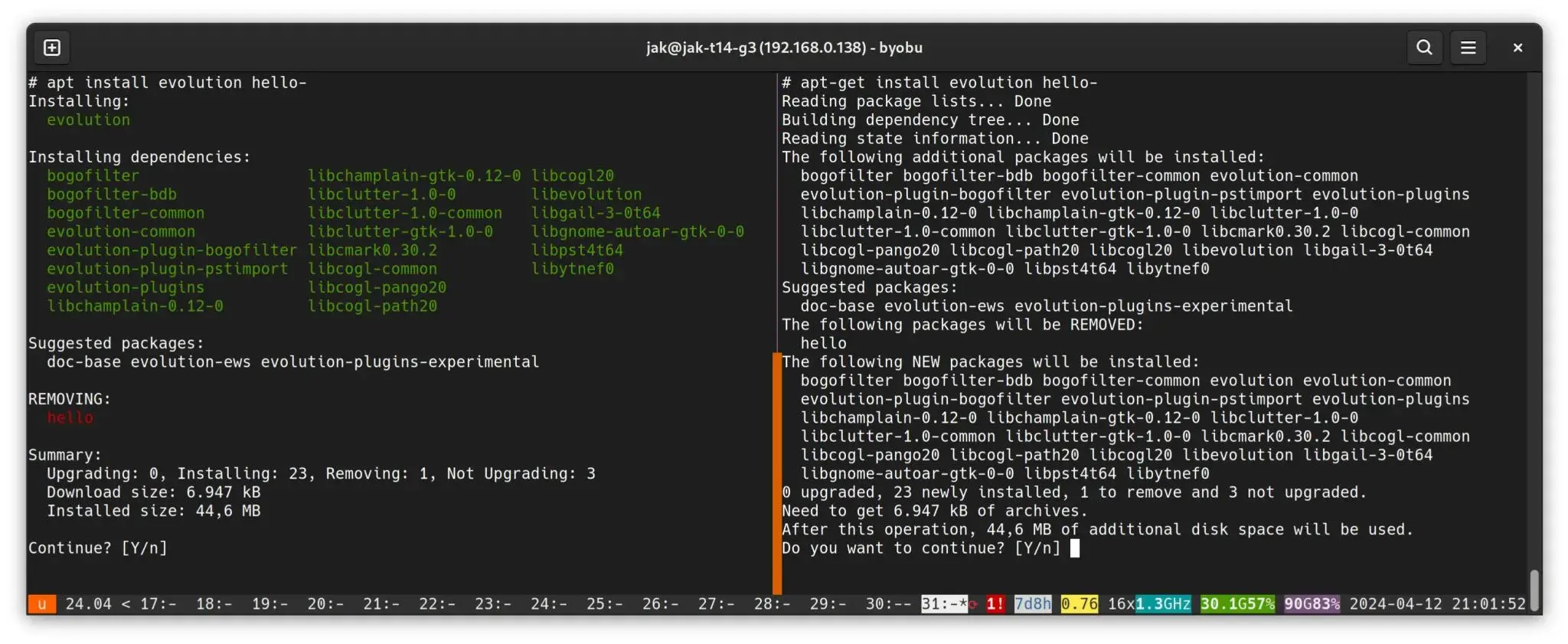
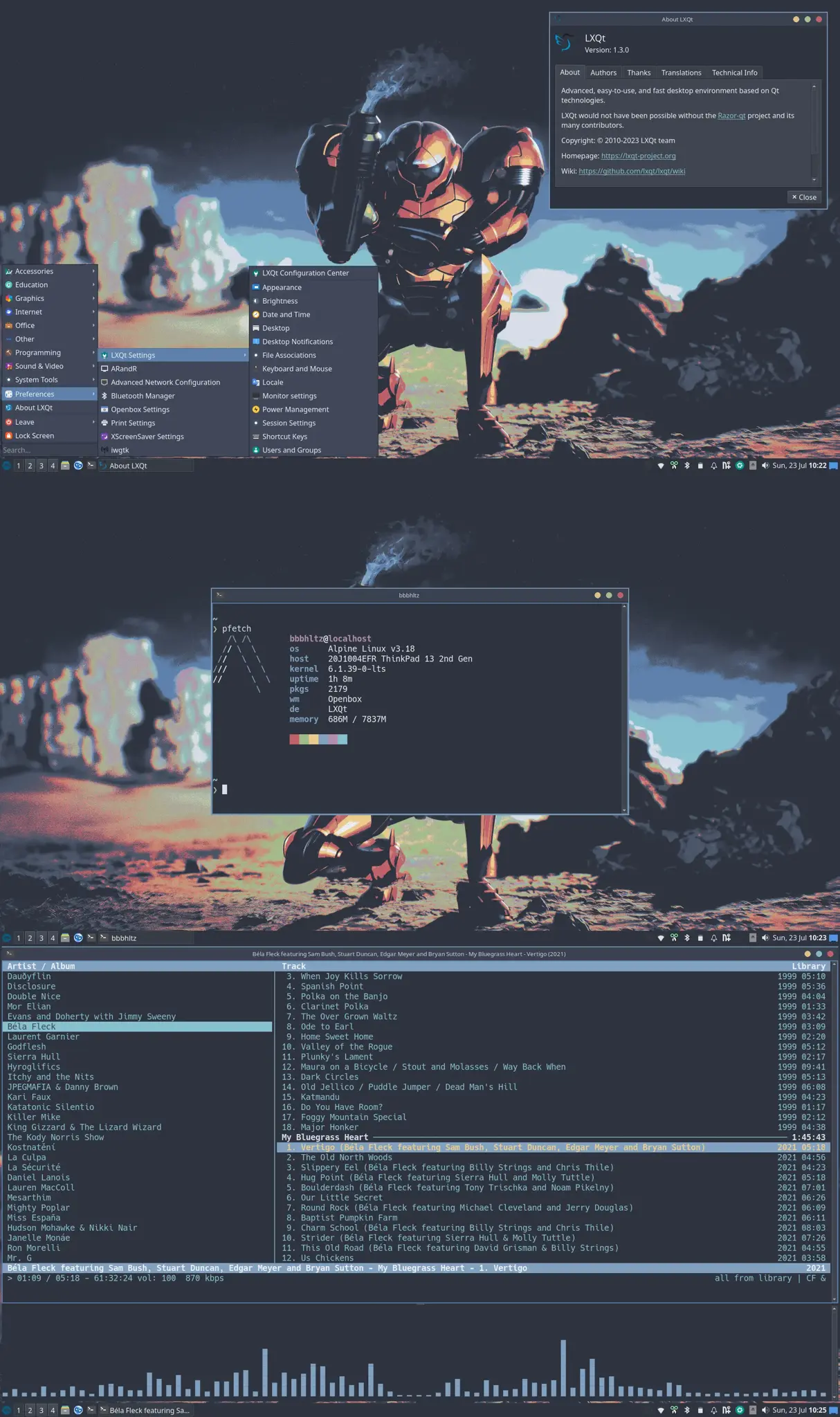
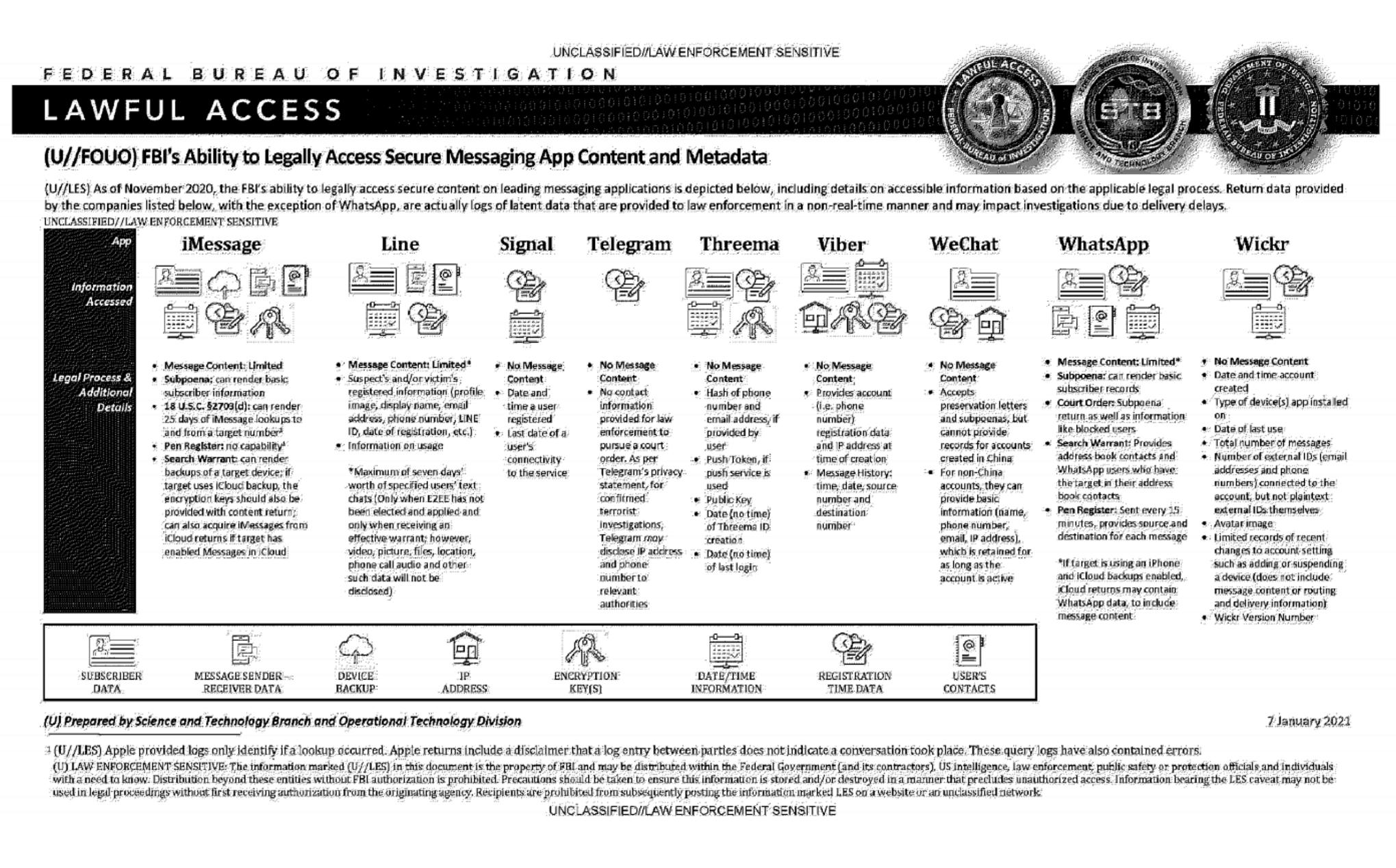

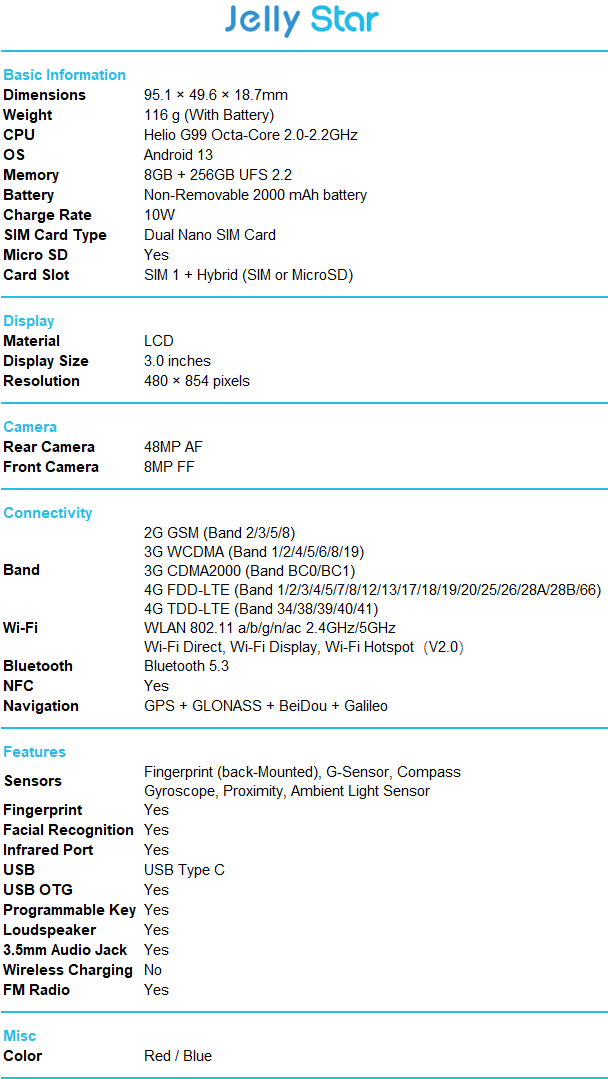
Hi,
It it possible that Plank doesn't work with Wayland, plain and simple.
https://bugs.launchpad.net/plank/+bug/1632841
The latest version dates back to 2019.
I think Dash to dock is used often.
For Guake the version in Bookworm is from 2022 and you may need to set an environmental variable or perhaps it isn't built with Wayland support on Debian.
You could hit up the Debian forums for a better answer.