Edit: Solution
Yeah, thanks to u/postnataldrip@lemmy.world I contacted my ISP and found out that in fact they were blocking my port forwarding capabilities. I gave them a call and I had to pay for a public IP address plan and now it's just a matter of testing again. Thank you very much to everyone involved. I love you. It was Megacable by the way. If anyone from my country ever encounters the same problem I hope this post is useful to you.
Here's the original post:
Hey!
Ok, so I'm trying to figure this internet thing out. I may be stupid, but I want to learn.
So, what I'm essentially doing is trying to host my own raw html website on my own hardware and get it out to the internet for everyone to see (temporarily of course, I don't want to get in trouble with hackers and bots) I just want to cross that out of my bucket list.
What I've done so far:
- I set up a qemu/kvm virtual machine with debian as my server
- I configured a bridge so that it's available to my local network
- I got my raw html document
- I'm serving it locally with nginx
- I tried to set up port forwarding (I get stuck here)
Right now everyone in my home can see my ugly website if they go to 192.168.1.114:8080 (since I'm serving it through port 8080).
However, I want to be able to go outside (I'm testing it with my mobile network using mobile data) to see my website.
I've configured port forwarding on my ZTE router (ISP-issued) with the following parameters:
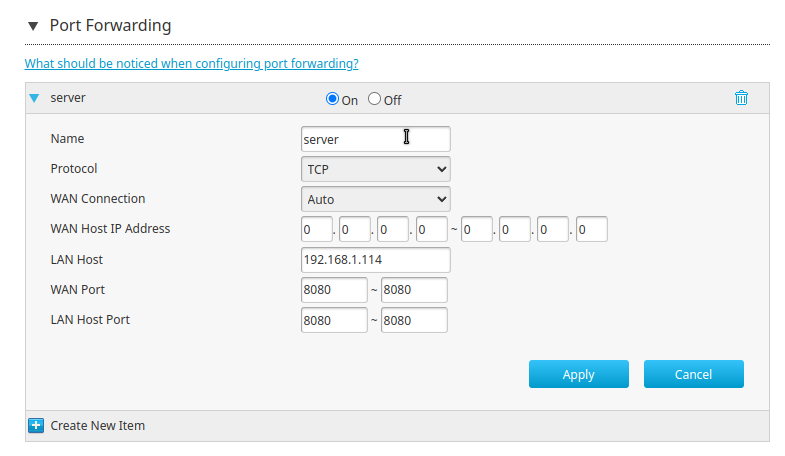
But now, if I search for my public IP address on my phone I don't get anything. Even if I go to my.public.ip.address:8080 (did you think I was gon-give you my public ip?)
I don't get anything. I've tried ping and curl. ping doesn´t even transmit the packages, curl says "Could not connect to server".
So, If you guys would be so kind as to point me in the right direction, I pose the following questions :
- How do I even diagnose this?
- What am I missing?
- Am I being too stupid?
- What do I do now?
(Here's a preview of my ugly website)
I also own a domain (with cloudflare) so, next step is getting that set-up with a DNS or something.
Thank youuuuuuu <3
It's probably a bit dangerous to expose your internal network in this way. If you really want a server running at home, there are interesting services which provide that for a fee, or you could set up a "reverse ssh proxy".
It's easier to do on some flavor of Linux, but you will set up a background service to ssh to a cloud server you rent, which links a local port on the cloud server to a local port on your home computer. You can then run a web service like caddy server on the cloud server to securely serve this port.
I realize this sounds rather complex, but something to look into and learn.
Your Caddyfile on the cloud server will look something like this:
And the service on your local will look something like this:
You will have to allow ssh on a non standard port (arbitrarily 2097 here), that way you can still use ssh on the standard port 22. I have some services running like this through a NAT for years.
This is nice to have, but it should be noted that doing it this way doesn’t mitigate much in the way of danger.
How does it not mitigate the danger? You are putting a secure web server in front of the tunnel rather than basically all traffic being forwarded to the port?
Well what “danger” are you talking about exactly? Traffic being forwarded to a port is not a danger. If the traffic being forwarded is going to a web server, proxying the exact same traffic through a different web server beforehand isn’t going to be any different.