this post was submitted on 23 Jul 2023
51 points (96.4% liked)
Piracy: ꜱᴀɪʟ ᴛʜᴇ ʜɪɢʜ ꜱᴇᴀꜱ
54083 readers
325 users here now
⚓ Dedicated to the discussion of digital piracy, including ethical problems and legal advancements.
Rules • Full Version
1. Posts must be related to the discussion of digital piracy
2. Don't request invites, trade, sell, or self-promote
3. Don't request or link to specific pirated titles, including DMs
4. Don't submit low-quality posts, be entitled, or harass others
Loot, Pillage, & Plunder
💰 Please help cover server costs.
founded 1 year ago
MODERATORS
you are viewing a single comment's thread
view the rest of the comments
view the rest of the comments



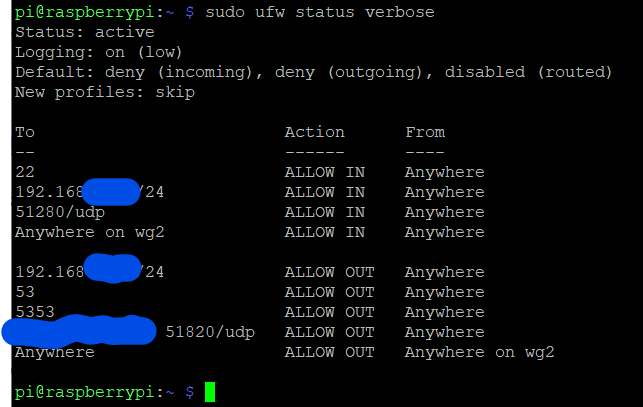
Pretty sure DNS is 53 UDP. Not sure if you meant it like that.
Port 53 TCP is for dns zone transfers
DNS vc is used for any dns request, not just zone transfers. UDP can sometimes fail in some situations, in which case the client will fall back to TCP which will keep it working.
I've got 53 and 5353 open so that DNS will work for my local network when connecting to *arr and jellyfin.
I.E. type raspberrypi:8989 in a browser to bring up Sonarr.
Should I restrict to UDP?
Just did some reading as it has been many years since I did firewall.. looks like dns is mostly UDP, but fails over to TCP if the dns reply exceeds 512bytes.
No, you should keep both udp and tcp port 53 open going out. blocking dns vc/tcp will result in dns being partially broken.