Give openappsec a try. It's not entirely Open Source, howerver you don't need to share anything with the company behind it (Check Point), and the solution "Just works" most of the time (fail2ban support included) without the hassle of adjusting a multitude of rules thanks to the use of AI. Just install and forget about it. I only had to create one custom rule, so the WAF would allow the upload of big files into my Nextcloud server. Keep in mind I only expose a couple of my own services to the Internet, that only me and couple of friends of mine will use, so I doubt I can be very representative here.
Selfhosted
A place to share alternatives to popular online services that can be self-hosted without giving up privacy or locking you into a service you don't control.
Rules:
-
Be civil: we're here to support and learn from one another. Insults won't be tolerated. Flame wars are frowned upon.
-
No spam posting.
-
Posts have to be centered around self-hosting. There are other communities for discussing hardware or home computing. If it's not obvious why your post topic revolves around selfhosting, please include details to make it clear.
-
Don't duplicate the full text of your blog or github here. Just post the link for folks to click.
-
Submission headline should match the article title (don’t cherry-pick information from the title to fit your agenda).
-
No trolling.
Resources:
- selfh.st Newsletter and index of selfhosted software and apps
- awesome-selfhosted software
- awesome-sysadmin resources
- Self-Hosted Podcast from Jupiter Broadcasting
Any issues on the community? Report it using the report flag.
Questions? DM the mods!
https://github.com/fail2ban/fail2ban
You can set dbpurgeage to 30d and pretty much just run it--or you can setup jail.conf with a bantime.factor. Its appeal is that you basically can download it, enable it, and it just works for you. It depends on your environment, though. If you have incoming authorized requests from other services it might be a pain to configure, but I've never used anything easier to protect you from bad actors.
fail2ban isn't a WAF?
I've used it on a machine before but given I am using a cloudflared container for ingress, can I route my traffic through a f2b container to the app? This might be ideal from a co fig perspective.
LLMs say yes but I'll need to play around.
Yes, you just have to enable the built-in plugin for cloudflared: https://github.com/fail2ban/fail2ban/blob/master/config/action.d/cloudflare.conf
Ahhhmazing, I'll set this up tonight. Really appreciate the help.
FYI, IP access rules don't count towards the 5 custom rules limit, but the more generous 50k limit.
With fail2ban, you can setup IP access rules via the cftoken-action quite easily.
Security --> WAF --> Tools to access the IP rules in the dashboard. https://developers.cloudflare.com/waf/tools/ip-access-rules/
I have more than 50k but even that page doesn't recommend it.
Top of that page
Recommendation: Use WAF custom rules instead
Cloudflare recommends that you create WAF custom rules instead of IP Access rules to perform IP-based or geography-based blocking (geoblocking):
- For IP-based blocking, use an IP list in the custom rule expression.
On the fail2ban front, can I run my traffic through a f2b container and out into my app?
WAF custom rules are more flexible, of course, and from a business perspective, I can understand why they would recommend that option instead.
I currently filter on an nginx access log file among other filters (sshd, bot-search, bad-requests) and let fail2ban execute the ban/unban action itself.
From a quick search, it should be possible to handle bans/unbans externally, if that's what you're after.
No I think f2b handling it would be totally fine for me. Kids got in the way with digging around too much but will try this week.
If you want to DIY something, I have a bash script that builds OpenResty with NAXSI from source. Most of the web apps I write anymore are actually in Lua, for OpenResty, maybe with an API written in something else. But I also help other members of my team deploy their Node and Python apps and stuff, and I always just park those behind OpenResty with NAXSI, just doing a standard nginx reverse proxy.
How easy is it to configure?
My goal is to download some lists from github and generate one big ban list to feed into the WAF but the community lists of Crowdsec might negate the need.
There's a learning curve, but if you're familiar with WAF's it's not hard.
Wafs don't make you safer but create unnecessary attack surface. Just keep your machine and services up to date.
I'm trying to block the most likely attack vectors which is definitely VPS providers at this point in time. I just figure if I am blocking subnets plus additionals I identify it will force them out of these vectors to attack in ways I might be able to report better abuse.
Here check out my analysis.
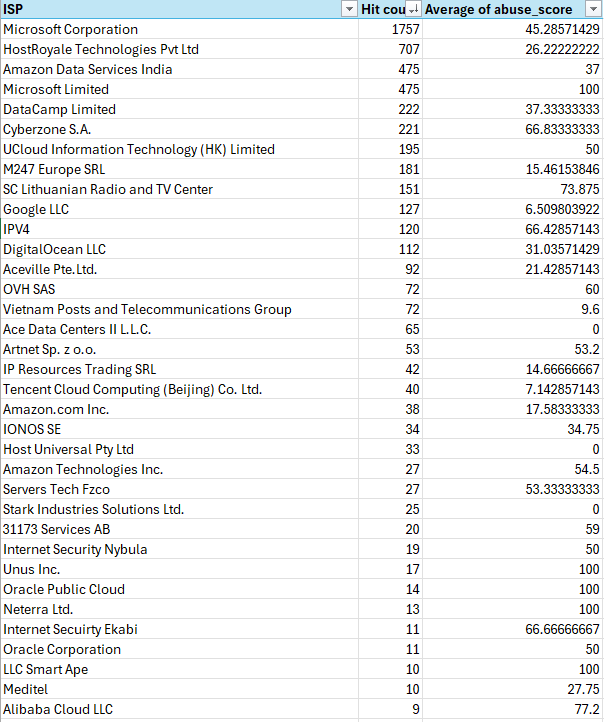
You will need to explain a bit further this statement to mild knowledged internet stranger....
Because the point of waf is exactly about reducing the exposed surface....